【AMD Zen架构将带来SME, SEV以及基于硬件的SHA等独家加密特性】AMD x86 Zen Architecture Will Implement Game Changing Encryption Features Such as SME, SEV and HW Based SHA ? Not Present In SkyLake or KabyLake
Today I will be talking about a very disruptive feature that will be present in AMD’s upcoming compute architecture. Disruptive is probably the most misused word in the history of technology and I do not use it casually. While the readers of this site consist primarily of technology enthusiasts, for whom this news may not mean much. From a company like AMD’s standpoint, a vast majority of revenue will come from the Enterprise segment. For Enterprise users, data security is a very important consideration and on that front AMD Zen will be introducing some very significant advanced encryption features, such as SME and SEV. These features are not present in any competing Intel architecture.
【今天我要讲的是Zen架构的一个杀手锏特性。我们的读者大多数是硬件发烧友,对于你们来说这篇新闻可能没多大意义。但对于目前立场上的AMD来说,营收的主要部分还是来自企业级市场。对于企业用户,数据安全是极为重要的,因此AMD Zen将带来非常先进的加密特性:比如SME和SEV,这些特性在Intel同级别的任何架构中还未出现。】
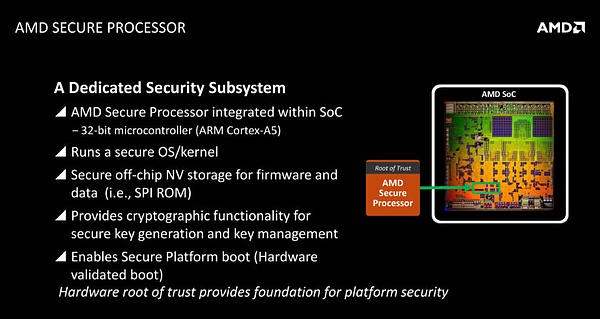
AMD Zen features SME (Secure Memory Encryption), SEV (Secure Encrypted Virtualization) and hardware based SHA powered by a security co-processor
【AMD Zen新增安全协处理器:将带来 SME(安全内存加密),SEV(安全虚拟化加密)以及基于硬件的SHA 】
There are two main features that I will be talking about in this article, alongside a third feature which in combination will make Zen a much sought out processor for the Enterprise sector. The first two are called SME and SEV, which stand for Secure memory Encryption and Secure Encrypted Virtualization. The third one is hardware based SHA. As I have mentioned before, at this moment, no competing Intel architecture has any known features to rival these. At the time of release, Zen will primarily compete against Skylake and Kaby Lake based processors, both of which lack the aforementioned features. It is not until Cannonlake and Coffe Lake that any semblance of parity is expected to be present between the two platforms ? and even then it won’t be complete.
【这三个特性将会使得Zen在企业级市场具有很大吸引力。头两个特性叫SME和SEV,意思是安全内存加密和安全虚拟化加密,第三个特性是基于硬件的SHA。到发布的时候, Zen的对手 – Skylake和Kaby Lake都缺少这些特性。直到Cannonlake和Coffe Lake才会出现部分类似的特性。】
All of this magic will happen, courtesy a “Security Co-Processor” that AMD has included inside of the Zen chip. Before we get into any explicit details ? let me explain what all of this fuss is about. Let me explain this by giving you the example of this very publication. WCCFtech is hosted on a VPS based platform that scales according to the traffic we get ? in other words, it’s hosted on the cloud. This means that we don’t have to pay for server resources we aren’t using and aren’t left stranded when traffic spikes. When we say it’s hosted on the cloud, what is actually happening is that we are serving our website via an instance of a virtualized server running on a physical server. This virtualized server can scale up or down (depending on the limits of the physical server) dynamically, according to the demand of the client and is hosted primarily in the RAM.
【这些都要归功于Zen内嵌的“安全协处理器”。比如我有一个网站,放在VPS上,根据负载自动增加资源,实际上就是放在了云端 — 你访问的就是一台物理服务器上运行的虚拟化服务器的一个实例。这个虚拟服务器可以自动调节资源。】
This essentially means is that all of our data, and potentially sensitive client details are stored in an unencrypted format inside the RAM of the servers. It also means that you have to trust your cloud hosting provider to not have malicious intent since any physical attack on the memory can be used to essentially get a copy of the virtualized server ? and all the cleartext data in it. This hasn’t been much of a problem of late because to do all of this, the attacker has to make sure the RAM does not lose power ? since volatile memory erases data beyond recovery as soon as power is lost. This makes attacks quite difficult (but not impossible) to execute. Two very important concepts come into play here: Virtualization and Volatile Memory. Intel based architectures currently do not contain any form of memory encryption technology that support virtualization. There is SGX, which stands for Software Guard Extensions but it is not something that can be taken as an alternative of Zen SEV/SME because unlike the former, it cannot be virtualized.
【这基本上意味着我们的所有数据,包括敏感用户数据,都以未加密的形式放在服务器的内存里。这同时意味着你的云服务提供商要良心,不会搞些偷鸡摸狗的事,不然任何物理内存攻击就直接可以换来虚拟服务器的一份拷贝 – 还有里面的所有明文数据。这个问题不算太大,因为攻击者必须保证内存不断电 – 不然RAM内的数据就会清掉。这使得攻击相当困难(但并不是不可能)。Intel服务器目前没有任何支持虚拟化的内存加密技术。现在只有SGX – Software Guard Extensions ,但这玩意不能被虚拟化,所以不如Zen的SEV/SME。】
Zen SEV ? the holy grail of secure cloud computing?
【Zen SEV – 安全云计算的救命稻草?】
With the advent of NVDIMM (non volatile memory) however, this is going to become a very big problem, very fast. Unlike inherently volatile DIMMs, non volatile memory does not lose all data and this lowers the difficulty bar for a cyber attack by several orders of magnitude. Since the data is in an unencrypted format in the memory, all an attacker has to do is to kill power to the memory and either physically take the memory or clone its contents. Everything inside it ? including passwords, confidential data, hashes ? would be in clear text format. To put it bluntly, NVDIMMs are jackpots for physical attack vectors.
【但随着NVDIMM(非易失性存储器)的逐步推进,这个问题马上就会变成大问题。NVDIMM不具有易失性存储器那种天生的断电丢数据特性,这会大大降低网络攻击的难度。因为内存里的数据都是未加密的,攻击者要做的就只有断电、拔走内存或者复制内容。里面的所有东西 – 包括密码、机密数据、号码 – 都是明文。说穿了,NVDIMM就是物理攻击者的新宝藏。】
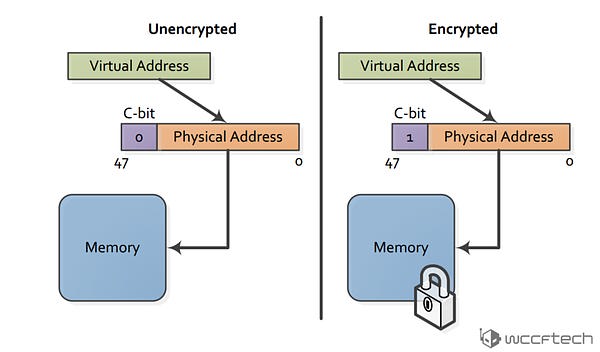
Enter Zen SME. Zen Secure Memory Encryption is something that allows the complete encryption of the memory being used. Your data is encrypted when it’s in transit on the internet. It has always been encrypted when it’s stored on an HDD or SSD in server farms. But the RAM is one place where it has always existed in clear text. With Zen SME, we can close the last remaining “cleartext” portion and enable encryption in the memory as well ? for truly end to end security.
【Zen上的SME则支持对正在使用的内存进行完全加密。你的数据在互联网上传输、存储在服务器的HDD或者SSD上的时候都是加密的,但在RAM里,它永远都是以明文形式存在。有了SME,我们可以加密内存,将这最后一扇“明文”的大门关上 – 实现真正的端到端安全。】
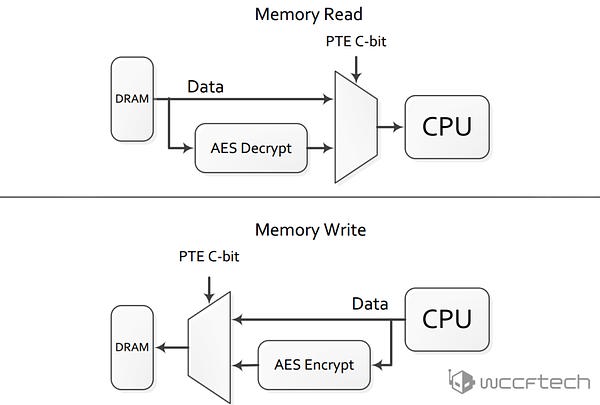
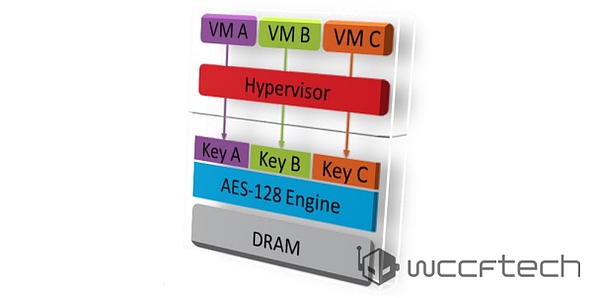
Main memory encryption is performed via dedicated hardware in the on-die memory controllers. Each controller includes a high performance Advanced Encryption Standard (AES) engine that encrypts data when it is written to DRAM, and decrypts it when read as shown. The encryption of data is done with a 128-bit key.
【主内存加密由集成的内存控制器上的独立硬件进行。每个控制器都有一个高性能AES引擎,可以加密写入DRAM的数据,在读取的时候再解密。加密技术为AES-128。】
As I have mentioned before, that Intel has something called Software Guard Extensions, but this particular instruction set cannot be virtualized since the silicon giant does not have any complete memory encryption standard. Thanks to SME, we get one more particularly useful feature: Zen SEV or Zen Secure Encrypted Virtualization.
【正如之前提到的,Intel也有SGX技术,但这个特殊指令集不能被虚拟化,所以Intel目前还没有与AMD相对抗的内存加密标准。多亏了SME,我们还能多一项特别有用的特性:Zen SEV – 安全加密虚拟化。】
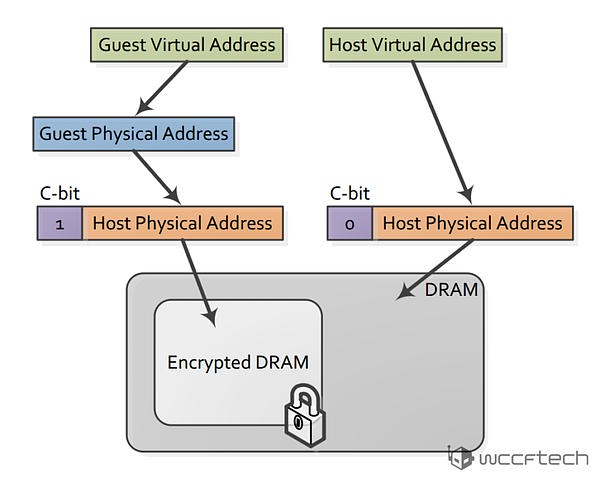
SEV is an extension to the AMD-V architecture which supports running multiple VMs under the control of a hypervisor. When enabled, SEV hardware tags all code and data with its VM ASID which indicates which VM the data originated from or is intended for. This tag is kept with the data at all times when inside the SOC, and prevents that data from being used by anyone other than the owner. While the tag protects VM data inside the SOC, AES with 128 bit encryption protects data outside the SOC.
【SEV是AMD-V架构的拓展,兹瓷在一个hypervisor管理下运行多个VM虚拟机。当SEV开启后,SEV硬件会给所有代码和数据加上名为VM ASID的tag,用来判断数据源自哪个虚拟机,或者是为了哪个虚拟机所准备的数据。只要数据还在SOC上,这个tag就会一直保留,阻止数据被所有者之外的其他人盗用。在SOC内部有tag保护数据,而在SOC外就是上面提到的AES128加密来保护数据。】
This is the holy grail of cloud computing (and security conscious individuals) and as the name states, will allow end users to encrypt the entire instance of virtualization. Not even cloud providers (who have physical access to the servers) will be able to carry out any malicious actions against their clients, if they were so inclined. For all intents and purposes, the data of consumers would be well and truly safe.
【这是云计算(以及对安全敏感的用户)的救命稻草,它能让用户加密虚拟化的整个实例。就算你的云服务提供商很无良,背后搞些小动作,加了密之后你的数据还是安全的。】
Zen will also contain hardware SHA ? which means it’s going to offer significant performance improvement over previous iterations of AMD architectures and even Intel offerings! As far as we know, hardware based SHA will not be present in Intel offerings till Cannonlake arrives and we have already listed the major disadvantage of SGX ? it cannot be virtualized. So at the time of launch, Zen processors will be the only competitive x86 chips around rocking hardware based SHA (and the accelerated performance that comes with it) as well as the security co processor powered SME/SEV security features. It remains to be seen when and if Intel will offer a competing solution to SEV.
【Zen也会带来硬件SHA – 这意味着新处理器的加解密性能提升会非常显著,甚至会超过intel!要知道,目前Intel还没有硬件SHA,直到Cannonlake才会有 – 然而我们在上面已经提了SGX的弊端 – 不能被虚拟化。因此在Zen发布的时间点,Zen将会是唯一一个具有硬件SHA加密、SME/SEV安全特性的X86处理器。接下来就等Intel出招了。】
source:http://wccftech.com/amd-zen-encryption-sme-sev-hw-based-sha/
自翻,转载请注明出处,严禁私自篡改标题、内容以及二次投递。